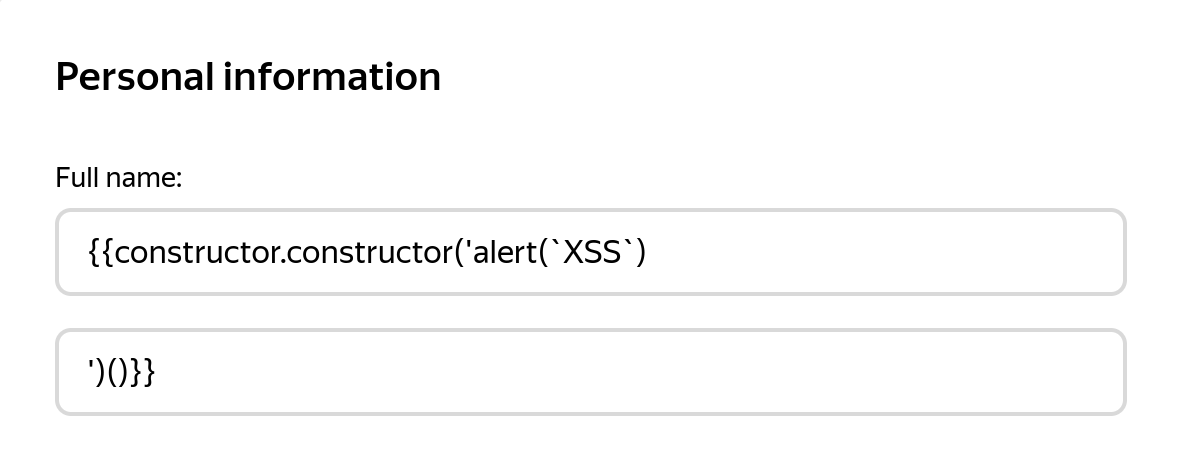
window.open(url, name) is vulnerable to XSS with name collision · Issue #262 · w3c/html · GitHub
Por um escritor misterioso
Descrição
Xiaoran Wang ([email protected]) This is a joint research with Travis Safford. window.open(url, name, [args]) makes it easy for websites accepting user supplied URLs to be vulnerable when attackers can cause a collision on the
NodeJS · GitHub
Connecting to WebDAV server on Microsoft Windows

Add support for inline JS/CSS with #attached [#2391025]
Cannot find name 'URL' · Issue #10498 · Azure/azure-sdk-for-js · GitHub

Ckan, PDF, File Format
GitHub - inforkgodara/xss-vulnerability: Explanation of Cross-site Scripting (XSS) with PHP mini project.

reactjs - WebStorm unable to recognise Next.js project - Stack Overflow
GitHub - cak/XSS-Challenge: A simple Cross-Site Scripting (XSS) challenge with multiple contexts and filters.

Persistent XSS (unvalidated Open Graph embed) at LinkedIn.com, by Jonathan Bouman
Security: window.open(url, name) is vulnerable to XSS with name collision · Issue #1509 · whatwg/html · GitHub
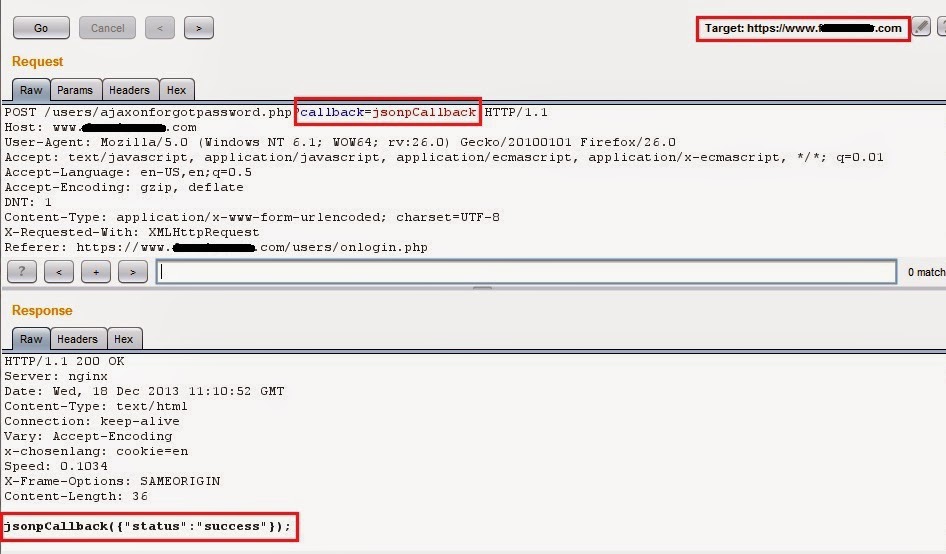
Cross Site Scripting through callback functionality
Warning] Stored XSS in TwoNav v2.0.28-20230624 · Issue #3 · tznb1/TwoNav · GitHub

writeups/bug.md at main · tess-ss/writeups · GitHub

Ckan, PDF, File Format
GitHub - payloadbox/xss-payload-list: 🎯 Cross Site Scripting ( XSS ) Vulnerability Payload List
de
por adulto (o preço varia de acordo com o tamanho do grupo)