BASHLITE Malware Uses ShellShock to Hijack Devices Running BusyBox - SecurityWeek
Por um escritor misterioso
Descrição
Shocker From Hackthebox. Shellshock and Perl equals to Shocker, by hac#
Shellshock Vulnerability and Attack
Shellshock Vulnerability Exploitation and Mitigation: A Demonstration

shellshock attack in #cybersecurity or #bash #bug #fyp

PDF) IOT Malware : An Analysis of IOT Device Hijacking

About the Shellshock Vulnerability: The Basics of the “Bash Bug” - Wiadomości bezpieczeństwa

Bashlite Updated with Mining and Backdoor Commands
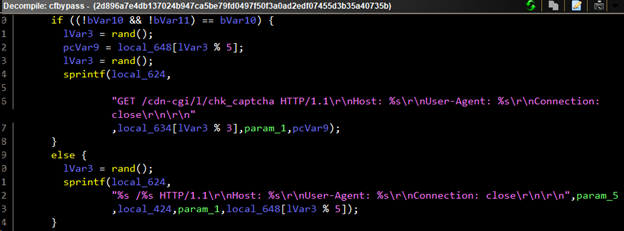
Bashlite Updated with Mining and Backdoor Commands

How to Exploit Shellshock-Vulnerable Websites with Just a Web Browser « Null Byte :: WonderHowTo
BASHLITE Malware Uses ShellShock to Hijack Devices Running BusyBox - SecurityWeek
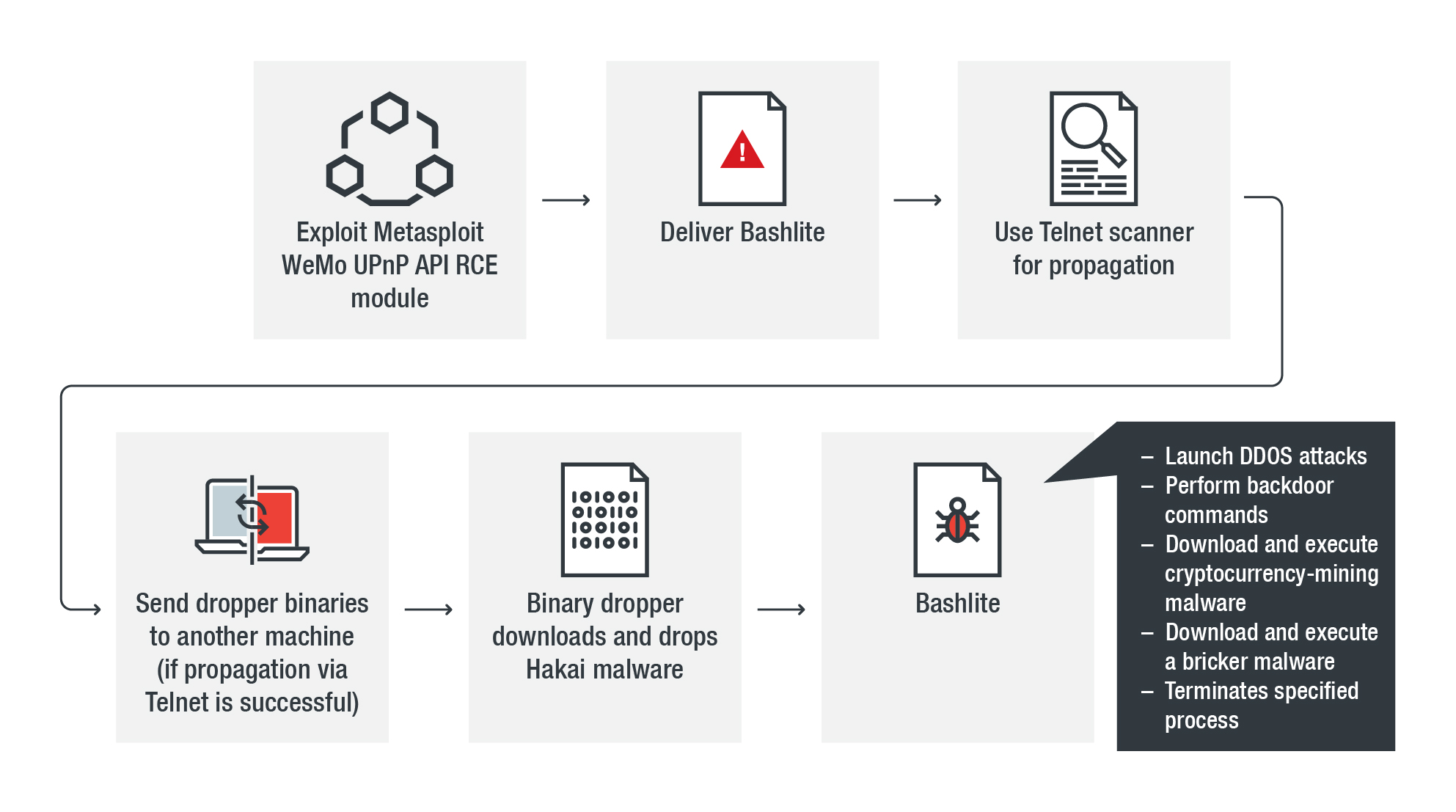
Bashlite Updated with Mining and Backdoor Commands

PDF) IOT Malware : An Analysis of IOT Device Hijacking
de
por adulto (o preço varia de acordo com o tamanho do grupo)



/i.s3.glbimg.com/v1/AUTH_08fbf48bc0524877943fe86e43087e7a/internal_photos/bs/2021/m/v/Q0cd1AQvKA9cNeleW85g/2014-09-29-shellshock2.png)



