Cryptojacking - Cryptomining in the browser — ENISA
Por um escritor misterioso
Descrição
The technique of hijacking browsers for mining cryptocurrency (without user consent) is called

ETL2020-Cryptojacking e BOOK EN- Enisa Amenaza #15 - From January

Cryptojacking: Has Your Computer Been Hijacked Yet? - Kratikal Blogs
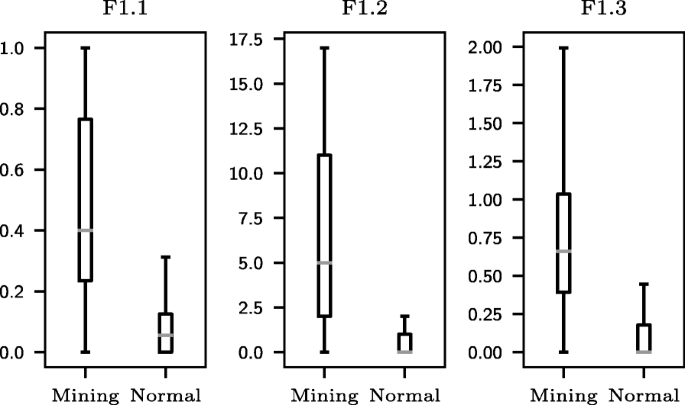
Detection of illicit cryptomining using network metadata

Awareness Articles – TPS ASAG – Application Security Awareness Group

PacNOG 23: Introduction to Crypto Jacking

What is cryptojacking and how does it work?

Cryptojacking: Has Your Computer Been Hijacked Yet? - Kratikal Blogs
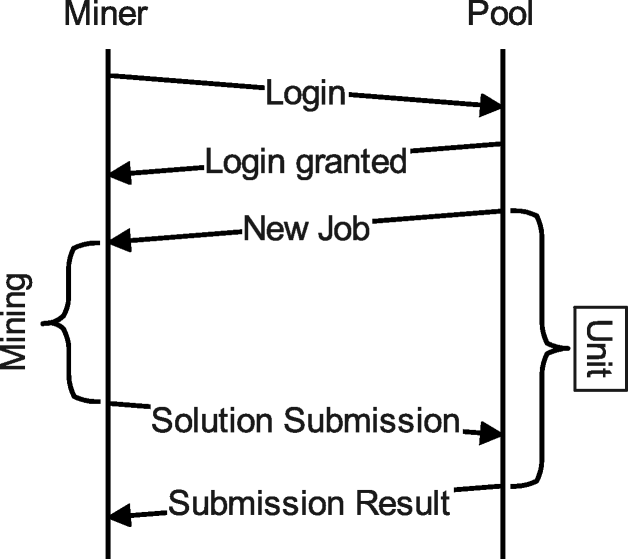
Detection of illicit cryptomining using network metadata

Reinforcing Financial Cybersecurity in the Eurozone by The

Cryptojacking (@cryptojacking) / X

Reading The ENISA Threat Landscape Report 2018

How Hackers Use Cryptojacking Malware to Take Over Computers to

Rundown of the Top 15 Cybersecurity Threats of 2019-2020 — Long Law

Black Arrow Cyber Threat Briefing 23 December 2022
de
por adulto (o preço varia de acordo com o tamanho do grupo)