No boundaries for Facebook data: third-party trackers abuse Facebook Login - Freedom to Tinker
Por um escritor misterioso
Descrição
by Steven Englehardt , Gunes Acar, and Arvind Narayanan So far in the No boundaries series, we’ve uncovered how web trackers exfiltrate identifying

First Amendment and free spech: When it applies and when it doesn't
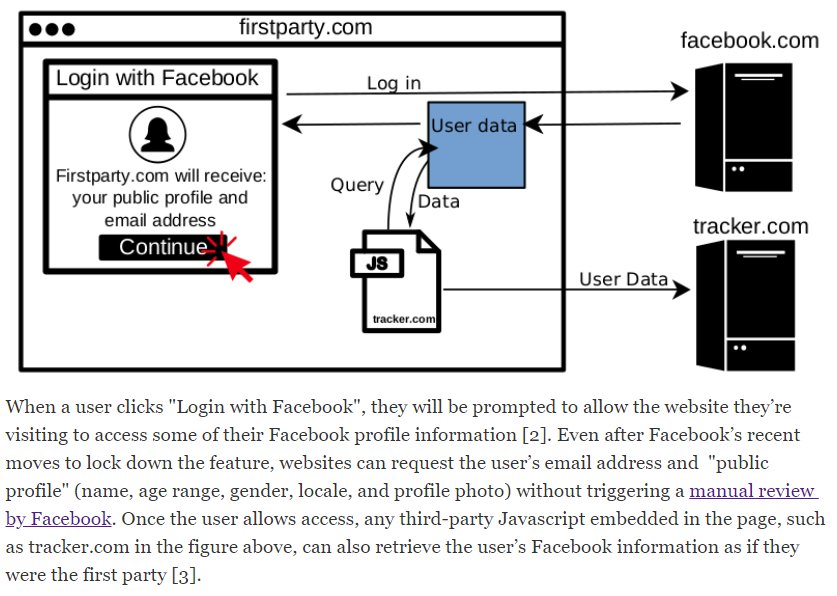
Arvind Narayanan on X: New research: third-party trackers wait for users to Login with Facebook, then exfiltrate user identifiers from Facebook by abusing the access that Facebook grants to the website.

Articles – Michigan Law Journal of Law and Mobility
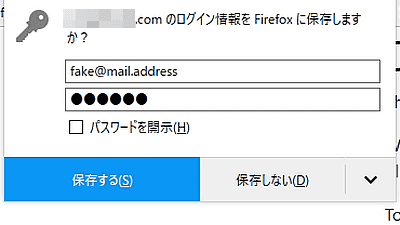
Web browser password manager steals user information vulnerability - GIGAZINE
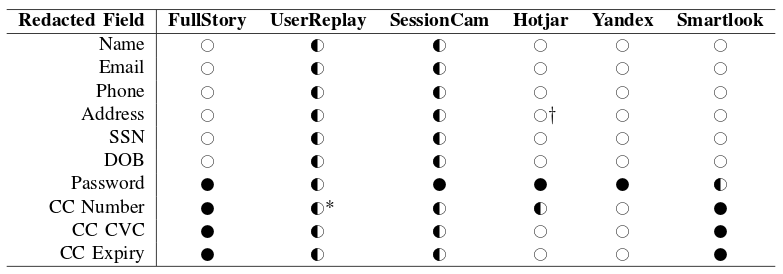
No boundaries: Exfiltration of personal data by session-replay scripts - Freedom to Tinker
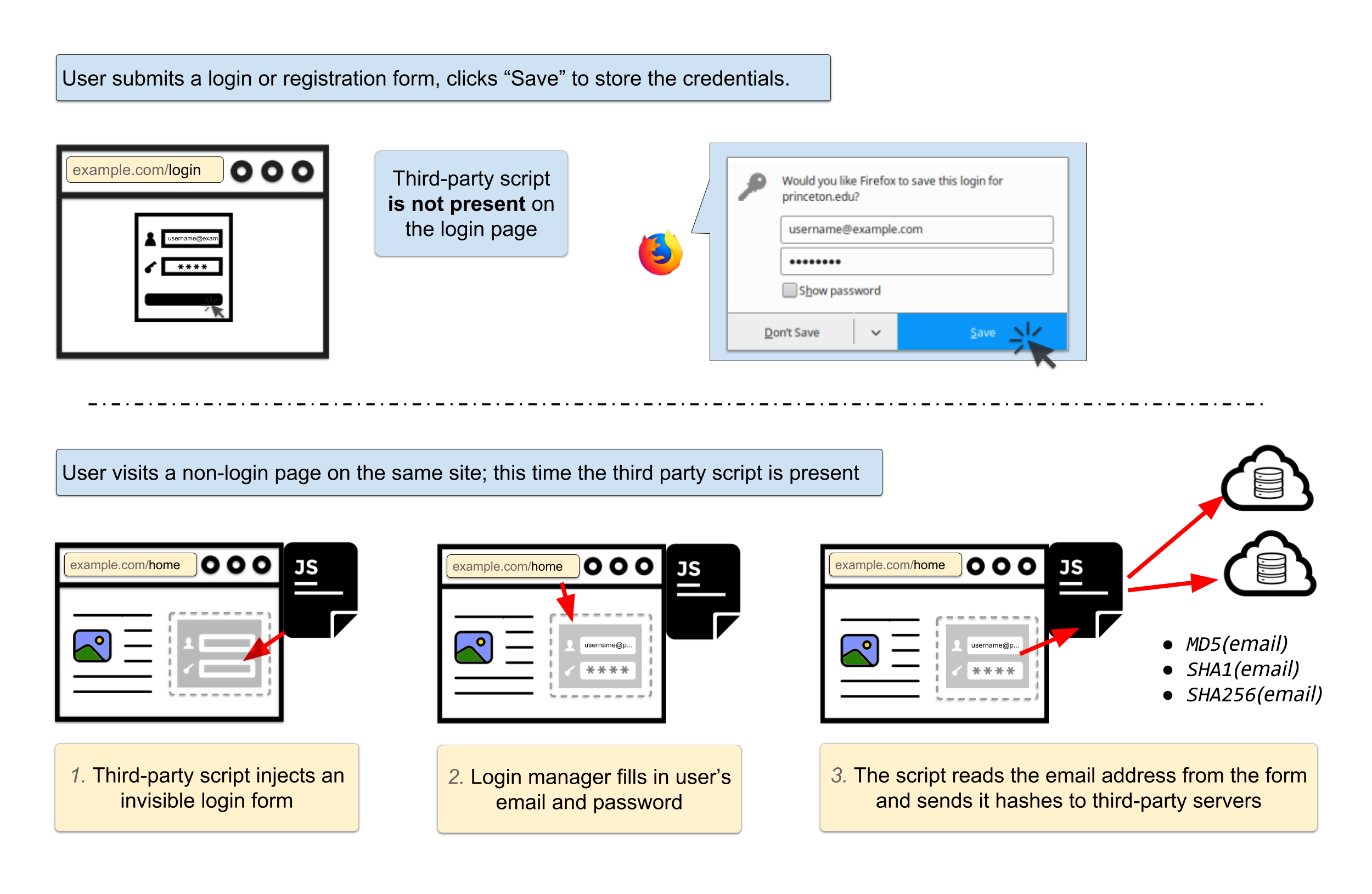
No boundaries for user identities: Web trackers exploit browser login managers - Freedom to Tinker

The Week USA 07.29.2022_downmagaz.net - Week july-York times-Biden

Mississippi Quarterly Vol. 74. No. 1 by Johns Hopkins University Press - Issuu
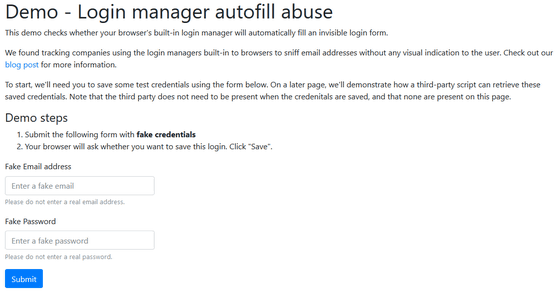
Web browser password manager steals user information vulnerability - GIGAZINE
PDF) No boundaries: data exfiltration by third parties embedded on web pages
de
por adulto (o preço varia de acordo com o tamanho do grupo)



/cdn.vox-cdn.com/uploads/chorus_asset/file/13293047/screen_shot_2018_09_28_at_1.21.04_pm.png)



:max_bytes(150000):strip_icc()/85-best-christmas-gifts-of-2023-tout-8745b504cc0b4c6eb3b24c3008a5504a.jpg)