Rundll32: The Infamous Proxy for Executing Malicious Code
Por um escritor misterioso
Descrição
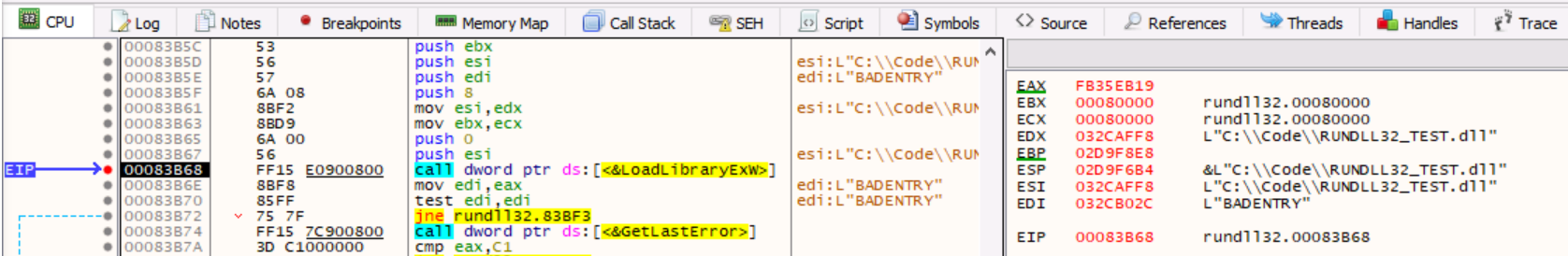
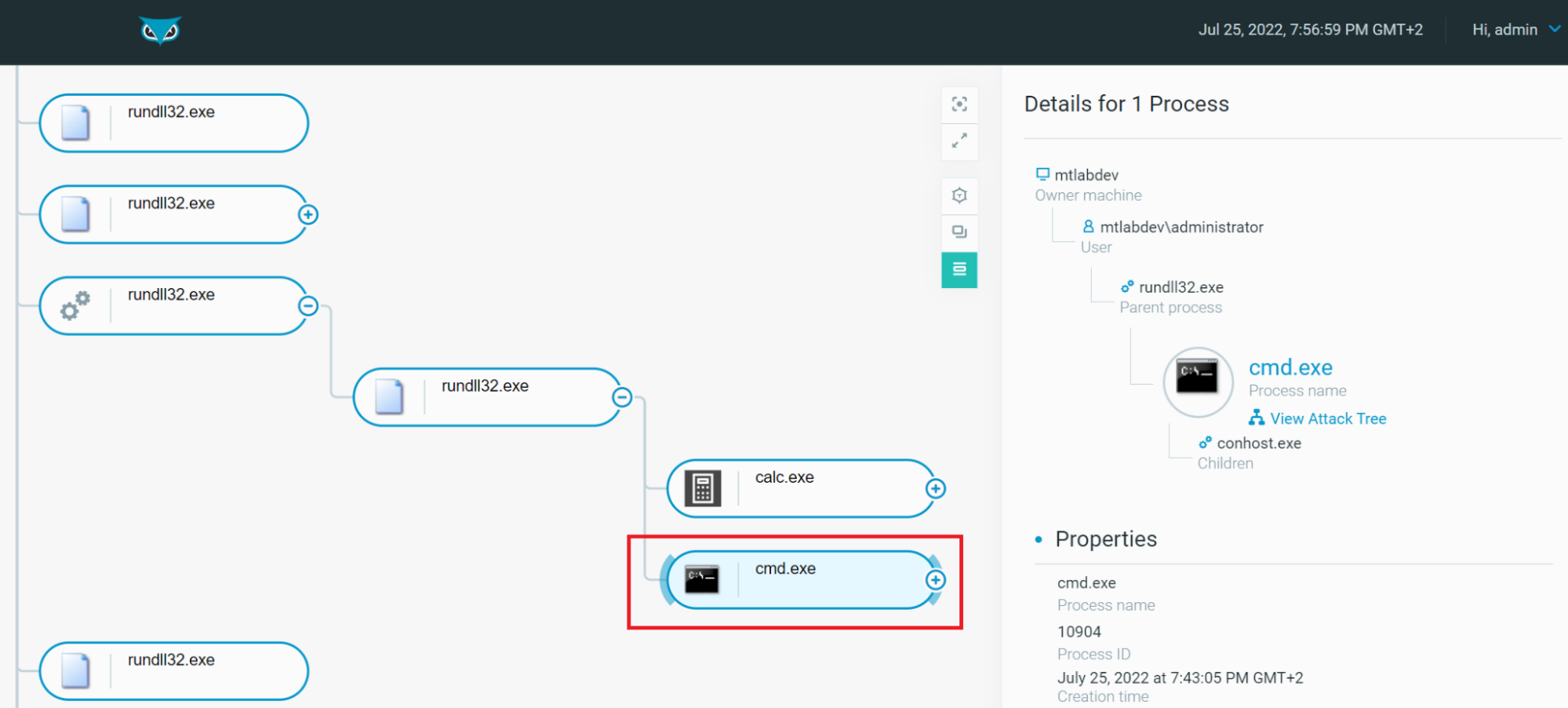
Take a deeper dive into an often abused Microsoft-signed tool, the infamous rundll32.exe, which allows adversaries to execute malicious code during their offensive operations through a technique which we explain in detail

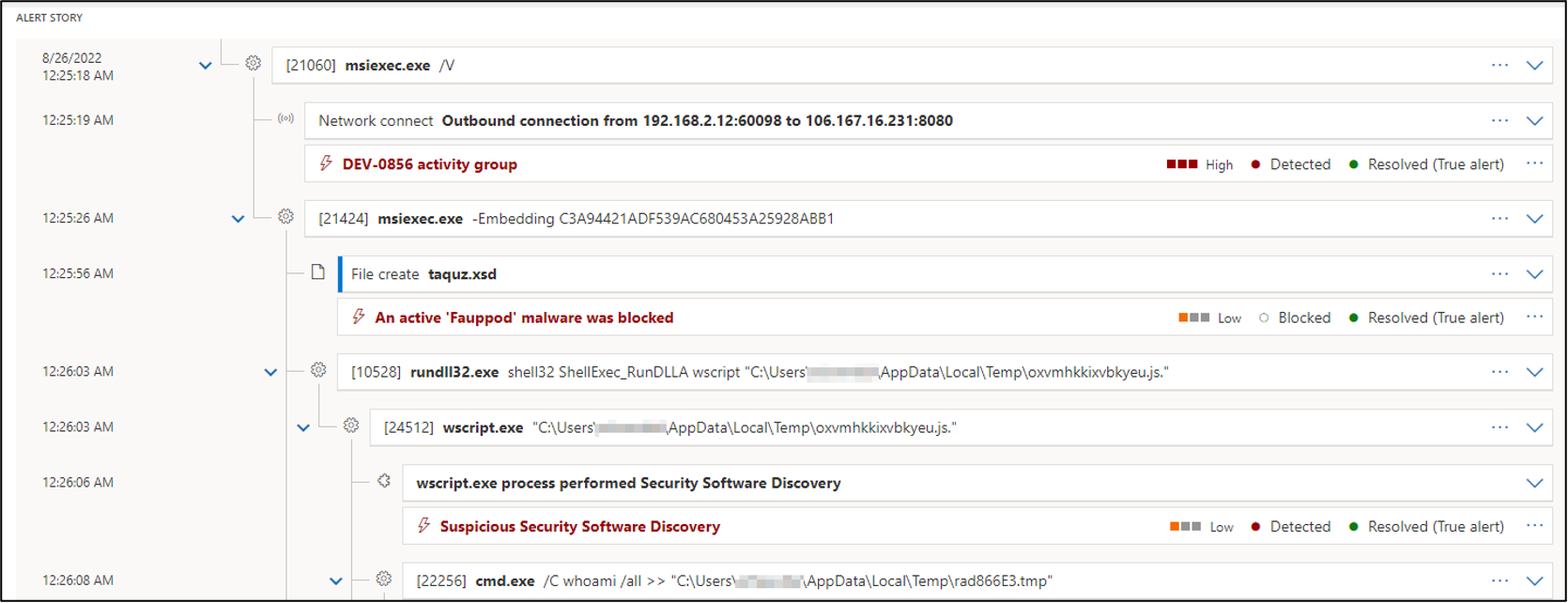
Microsoft experts linked Raspberry Robin malware to Evil Corp
themed campaigns of Lazarus in the Netherlands and Belgium

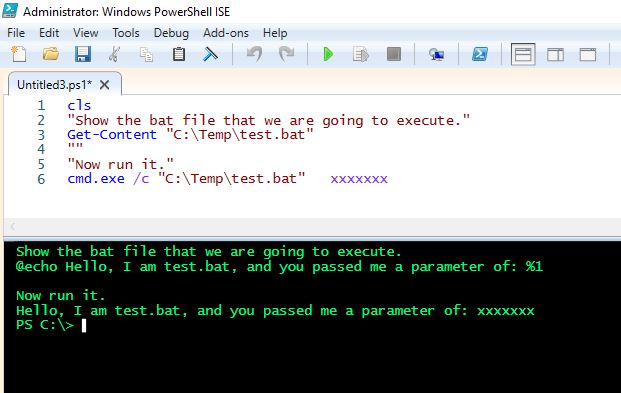
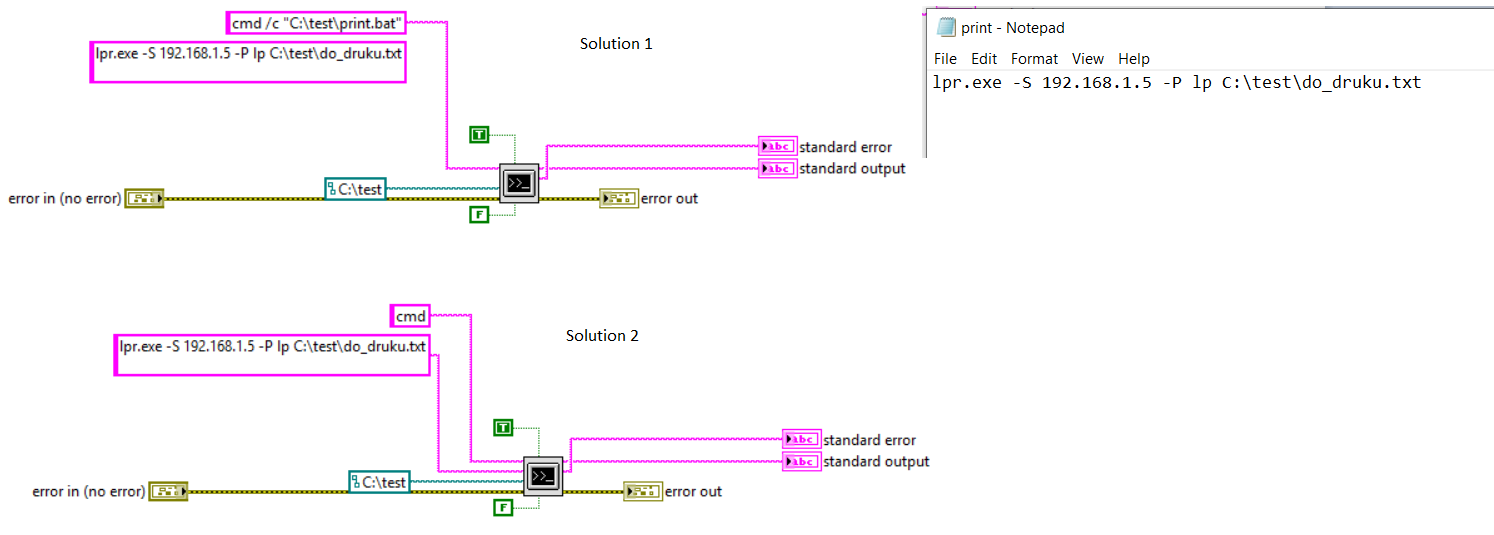
The second program that was found is rundll32exe which is a Microsoft signed
Rundll32: The Infamous Proxy for Executing Malicious Code
Rundll32: The Infamous Proxy for Executing Malicious Code
eSentire eSentire Threat Intelligence Malware Analysis: Raspberry…
FireEye Uncovers CVE-2017-8759: Zero-Day Used in the Wild to Distr - exploit database

Hackers use a new technique in malspam campaigns to disable Macro security warnings in weaponized docs

Swedish Windows Security User Group » ransomware
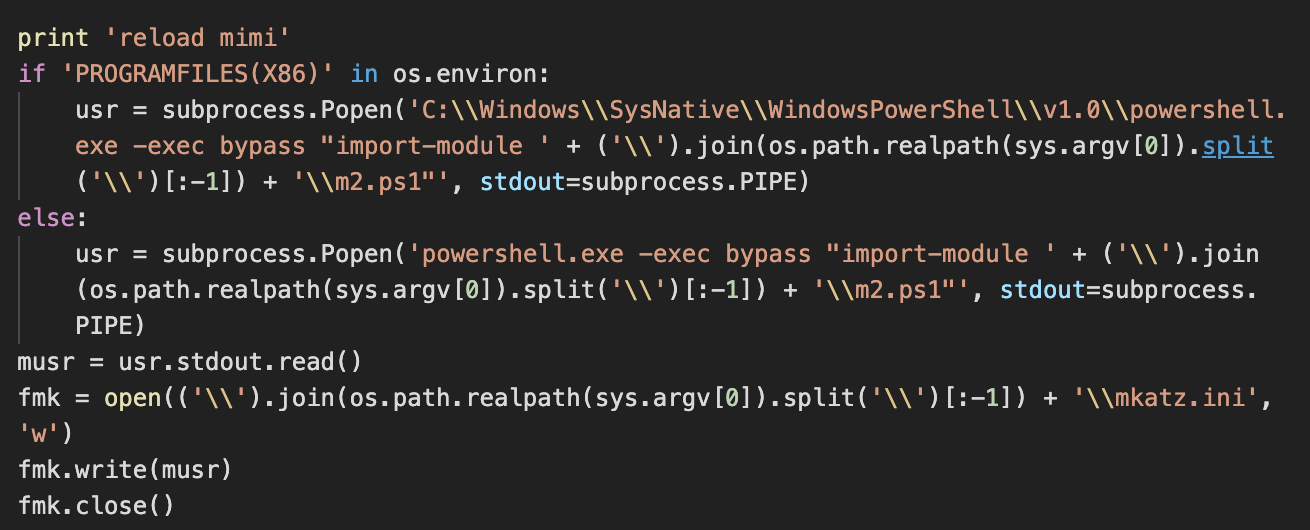
Lemon Duck brings cryptocurrency miners back into the spotlight

Rundll32: The Infamous Proxy for Executing Malicious Code

Rundll32 - Red Team Notes 2.0
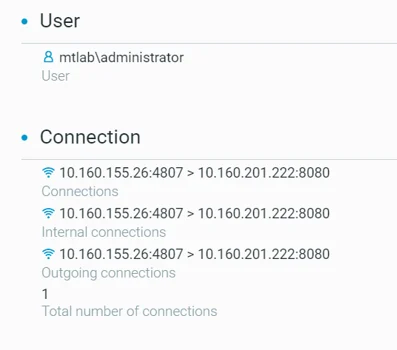
Rundll32: The Infamous Proxy for Executing Malicious Code

Amadey Bot Being Distributed Through SmokeLoader - Malware Analysis - Malware Analysis, News and Indicators
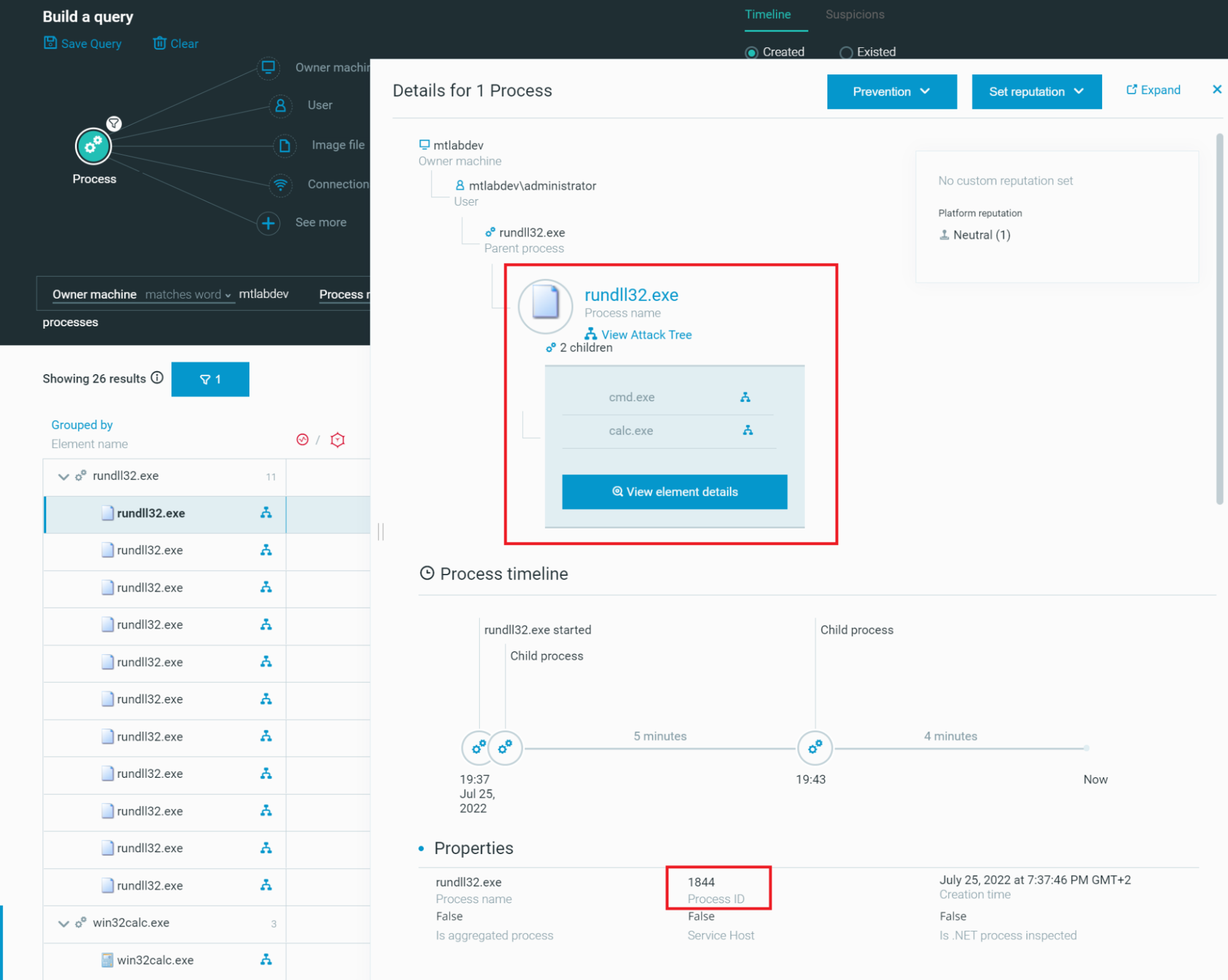
Rundll32: The Infamous Proxy for Executing Malicious Code
de
por adulto (o preço varia de acordo com o tamanho do grupo)