Bypassing XSS Defenses Part 1: Finding Allowed Tags and Attributes
Por um escritor misterioso
Descrição
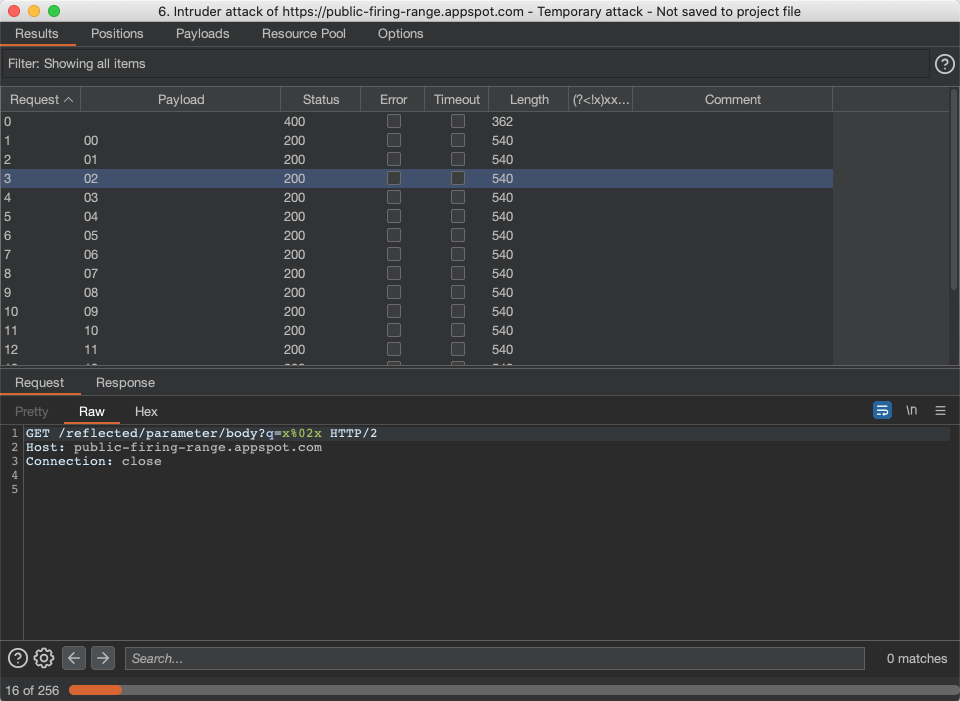
This post intends to serve as a guide for a common bypass technique when you're up against a web application firewall (WAF). In the event that the WAF limits what tags and attributes are allowed to be passed, we can use BurpSuite's Intruder functionality to learn which tags are allowed. Table of Contents: Setting the…
5 methods for Bypassing XSS Detection in WAFs

How to Find XSS Vulnerability: A Step-by-Step Guide & Tools

Bypassing XSS Defenses Part 1: Finding Allowed Tags and Attributes

Bypassing XSS Defenses Part 1: Finding Allowed Tags and Attributes

PDF) Cross-Site Scripting Attacks and Defensive Techniques: A Comprehensive Survey
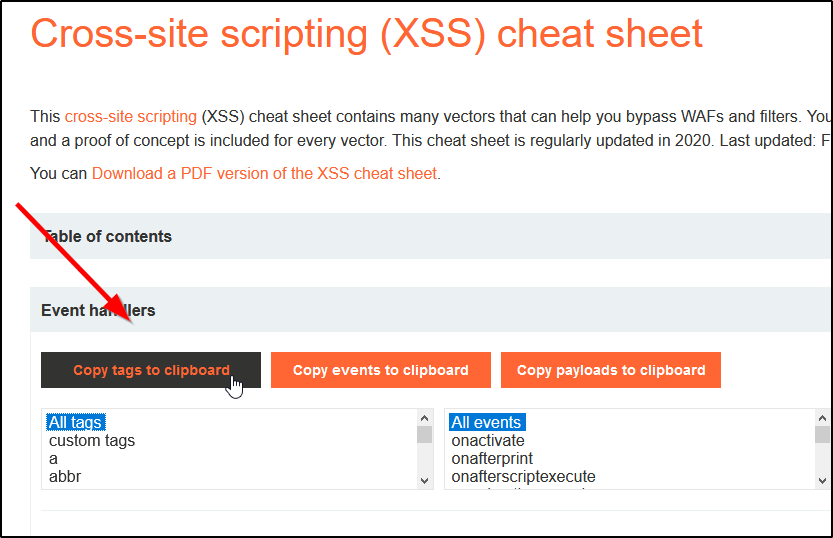
Bypassing XSS Defenses Part 1: Finding Allowed Tags and Attributes

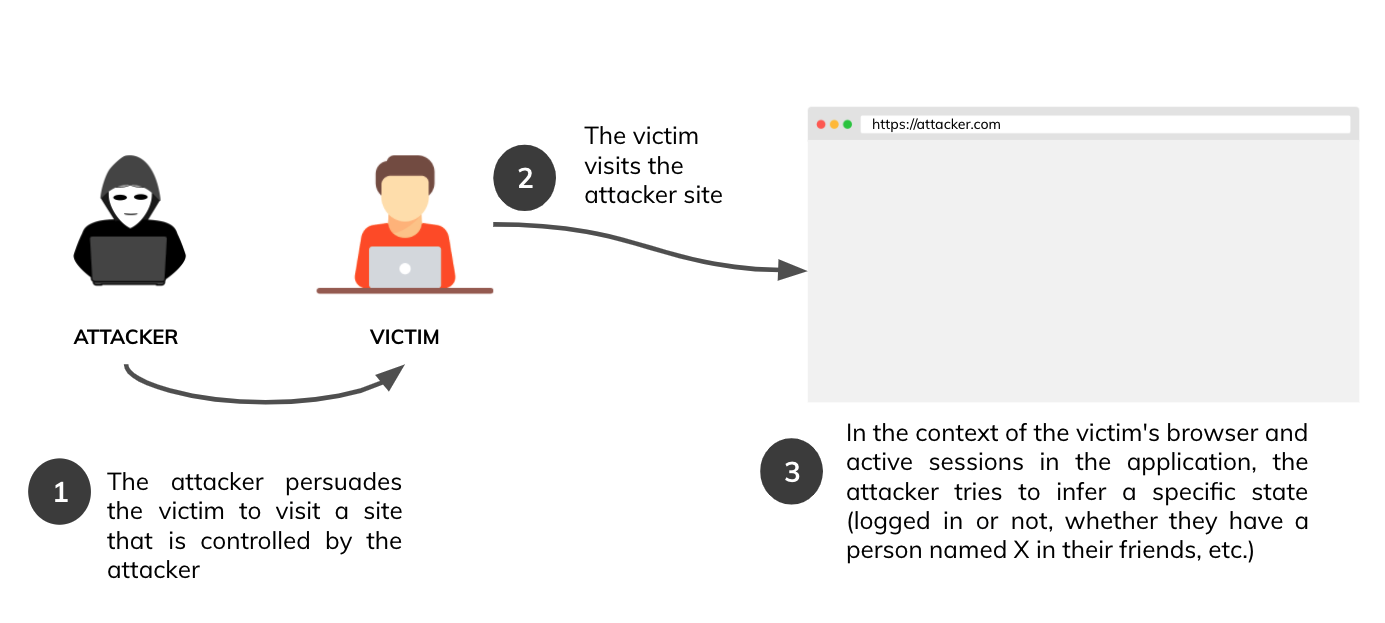
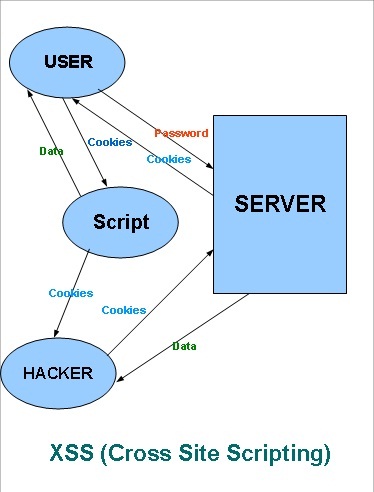
What is cross-site scripting (XSS)?, Tutorial & examples

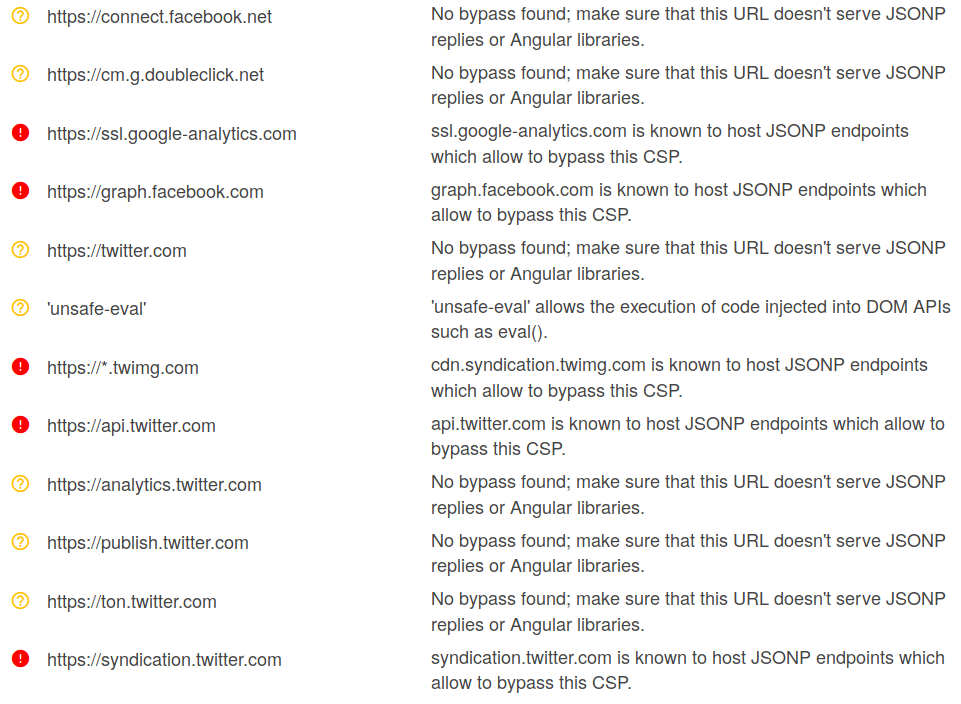
Reflected XSS protected by very strict CSP, with dangling markup attack (Video solution, Audio)

Node.js Security: Preventing XSS Attacks

Using an Interactive Cross-site Scripting Backdoor
de
por adulto (o preço varia de acordo com o tamanho do grupo)