Malware analysis Suspicious activity
Por um escritor misterioso
Descrição

Malware Analysis Tutorials: Complete Cheats Sheet - 2023

Malware Detection: 7 Methods and Security Solutions that Use Them
Highlight, take notes, and search in the book

Mastering Malware Analysis: A malware analyst's practical guide to combating malicious software, APT, cybercrime, and IoT attacks, 2nd Edition

Microsoft 365 Alerting - Detect and React to Threats Instantly

Intro to Malware Analysis: What It Is & How It Works - InfoSec
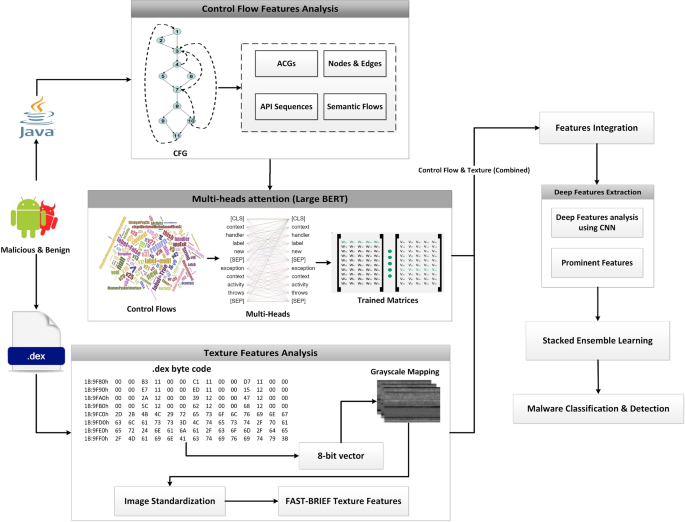
A malware detection system using a hybrid approach of multi-heads
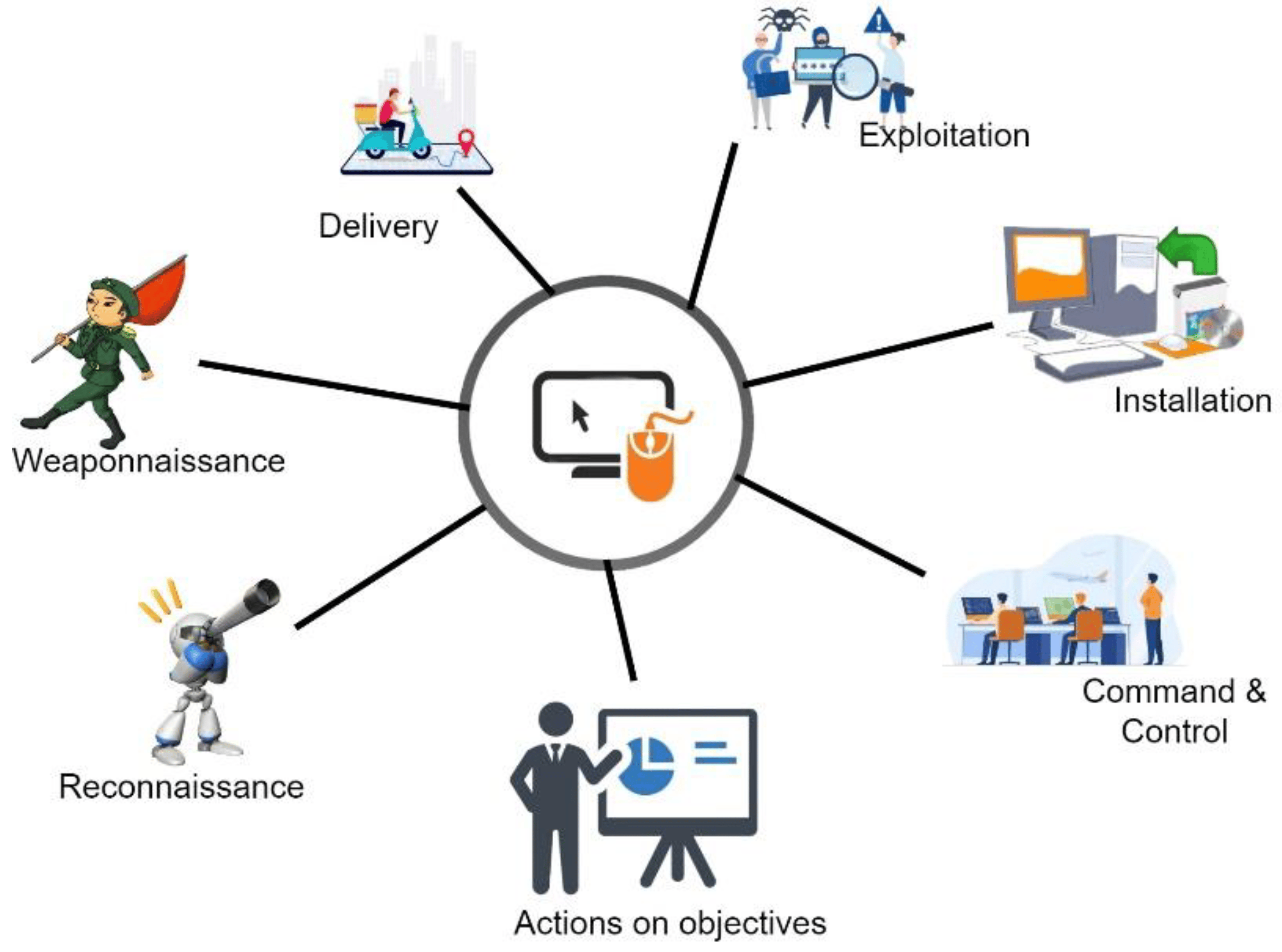
Symmetry, Free Full-Text

The General Behavior of Ransomware - Cisco Blogs

REMnux toolkit for malware analysis version 7 released - Help Net
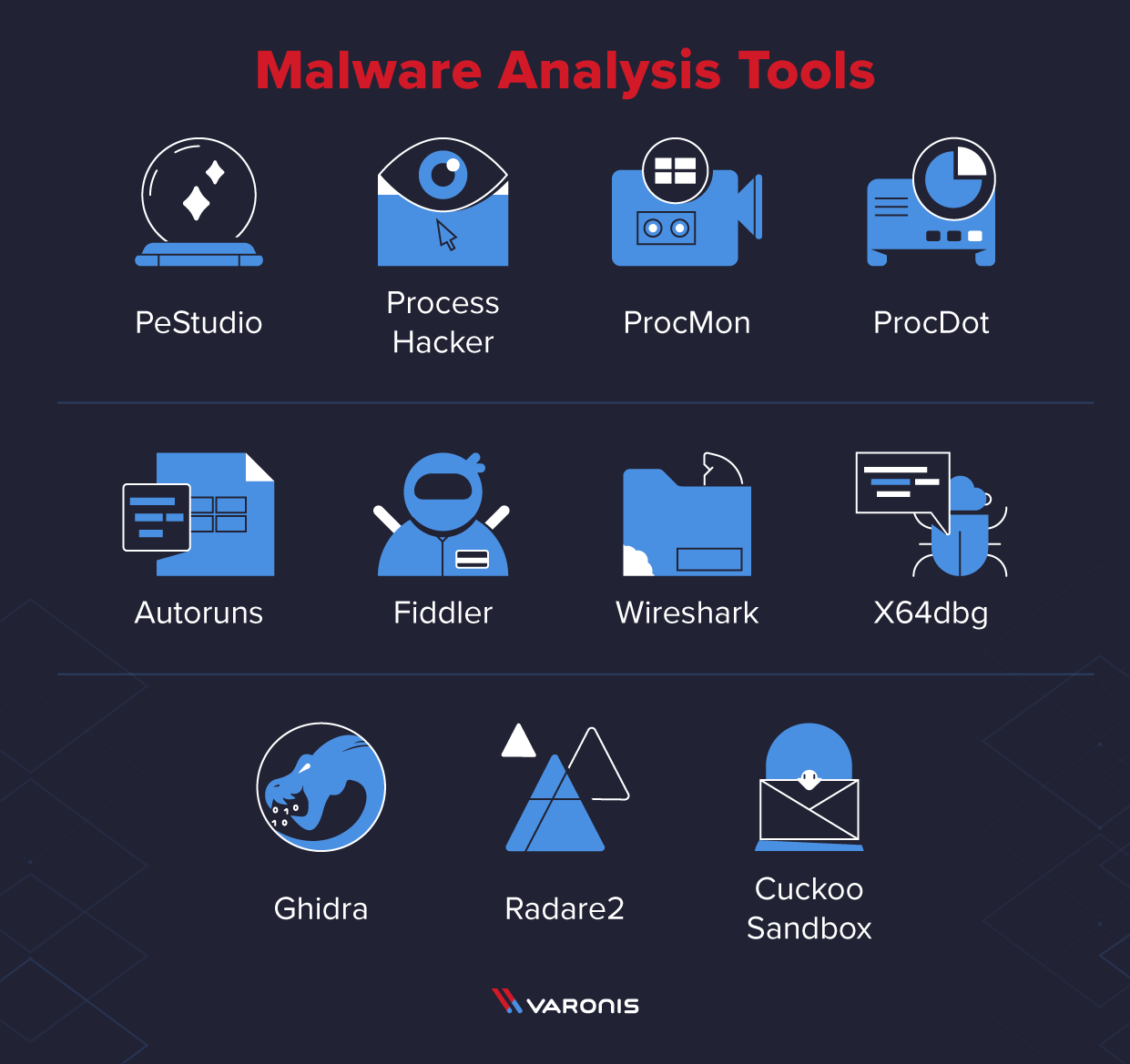
11 Best Malware Analysis Tools and Their Features
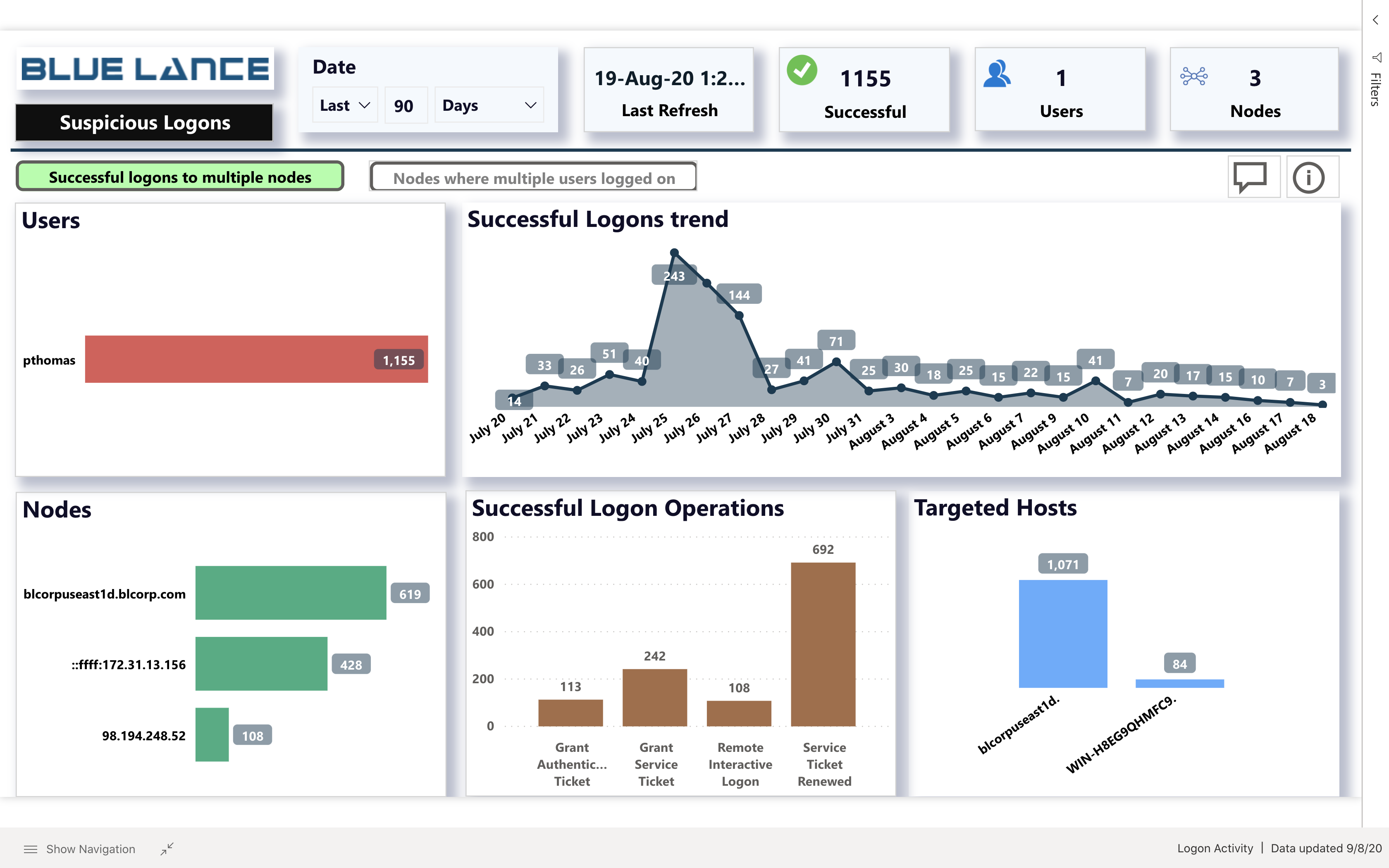
Suspicious Successful Logon Analysis
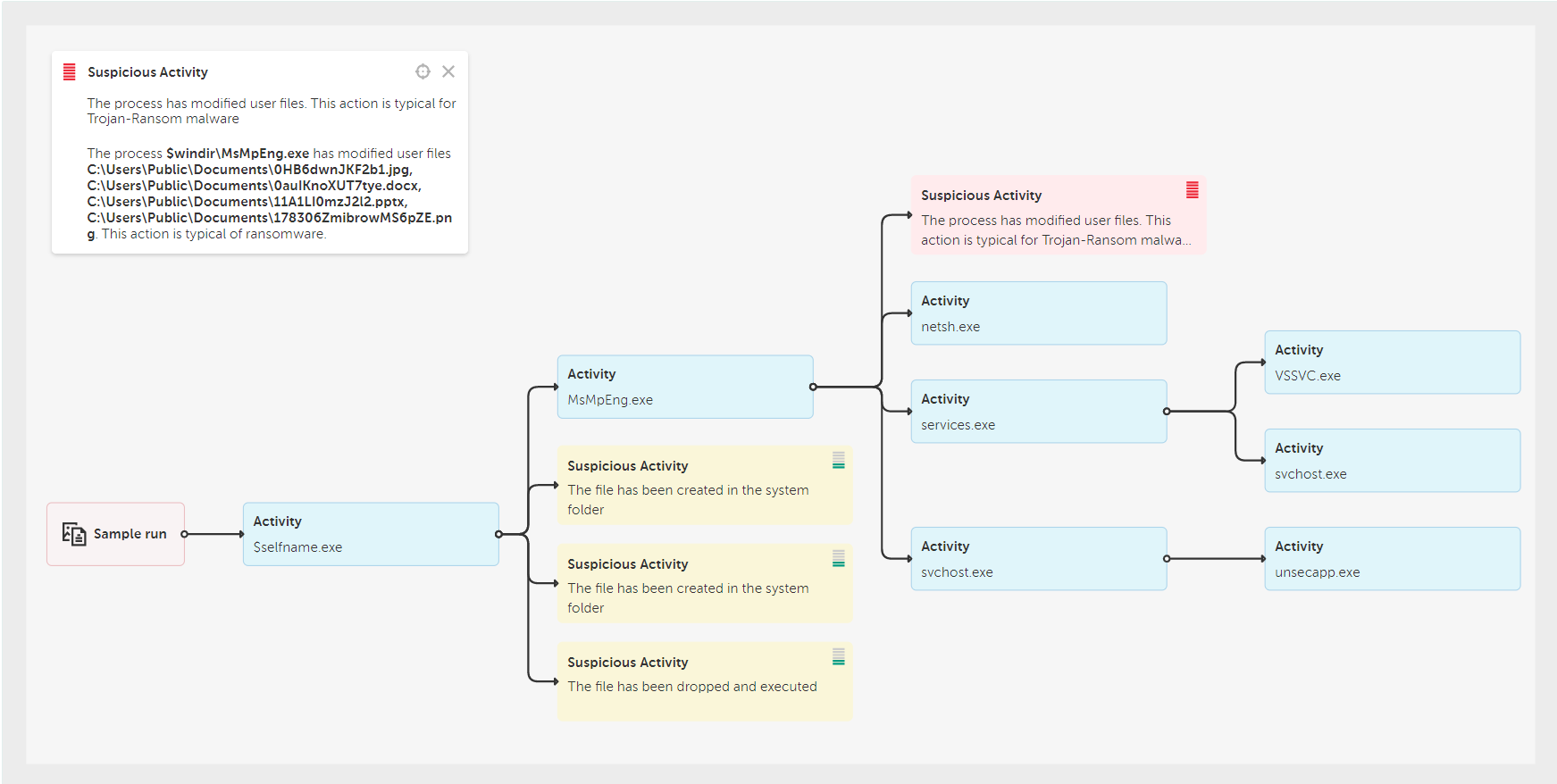
REvil ransomware attack against MSPs and its clients around the
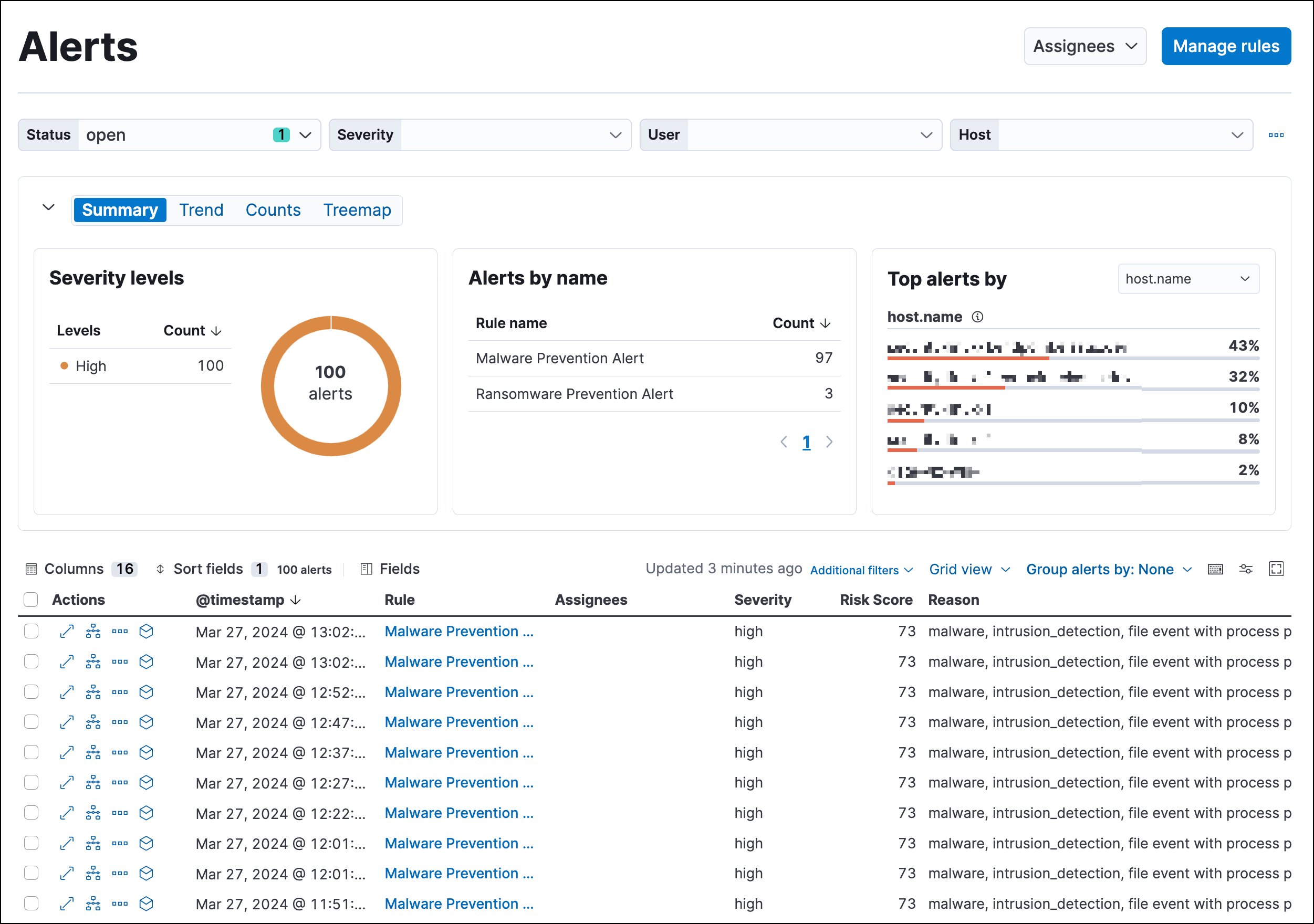
Detections and alerts, Elastic Security Solution [8.11]
de
por adulto (o preço varia de acordo com o tamanho do grupo)