Lab: Blind SSRF with Shellshock exploitation
Por um escritor misterioso
Descrição
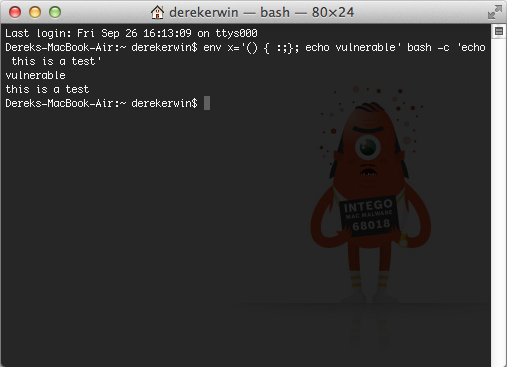
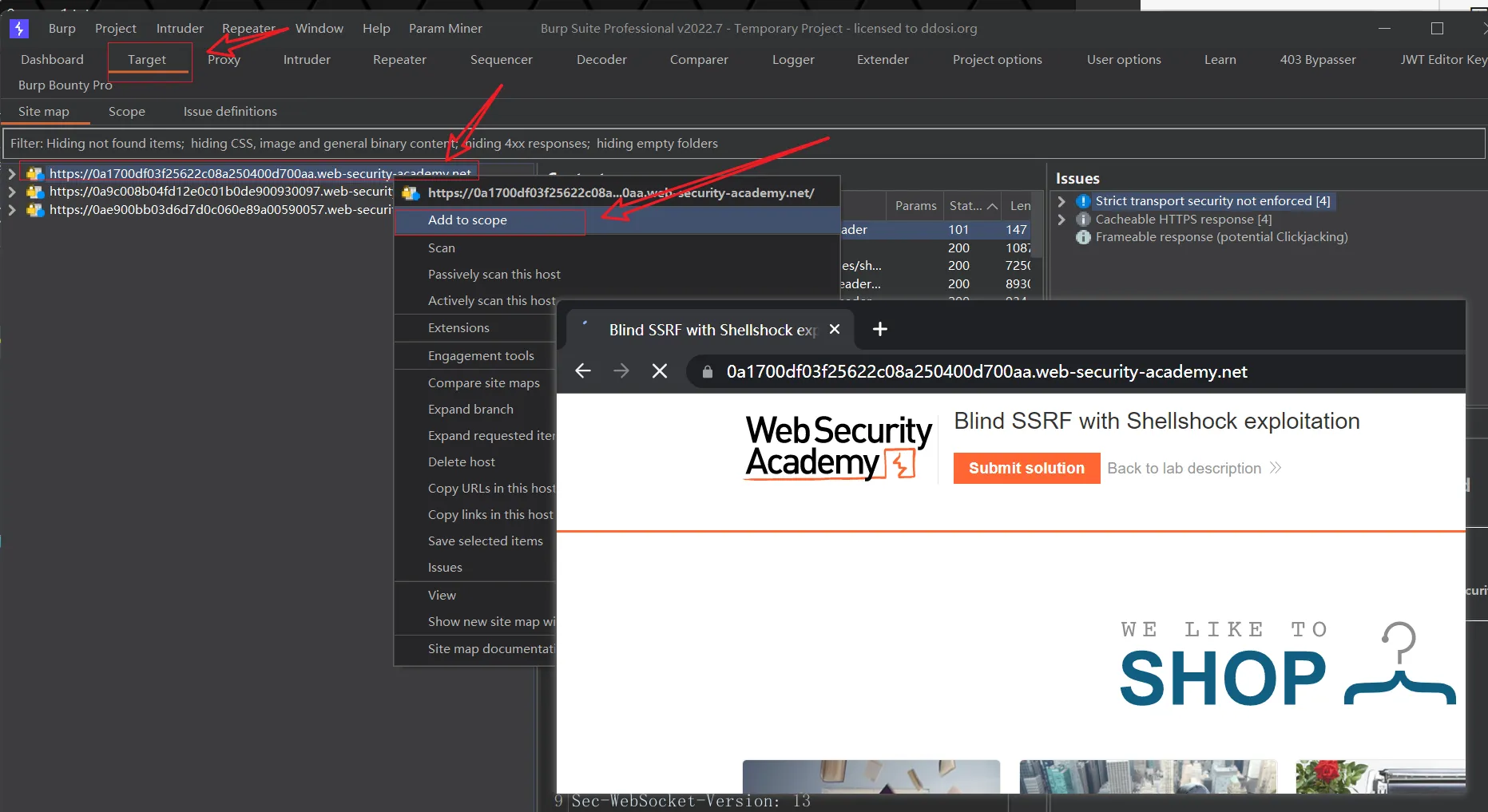
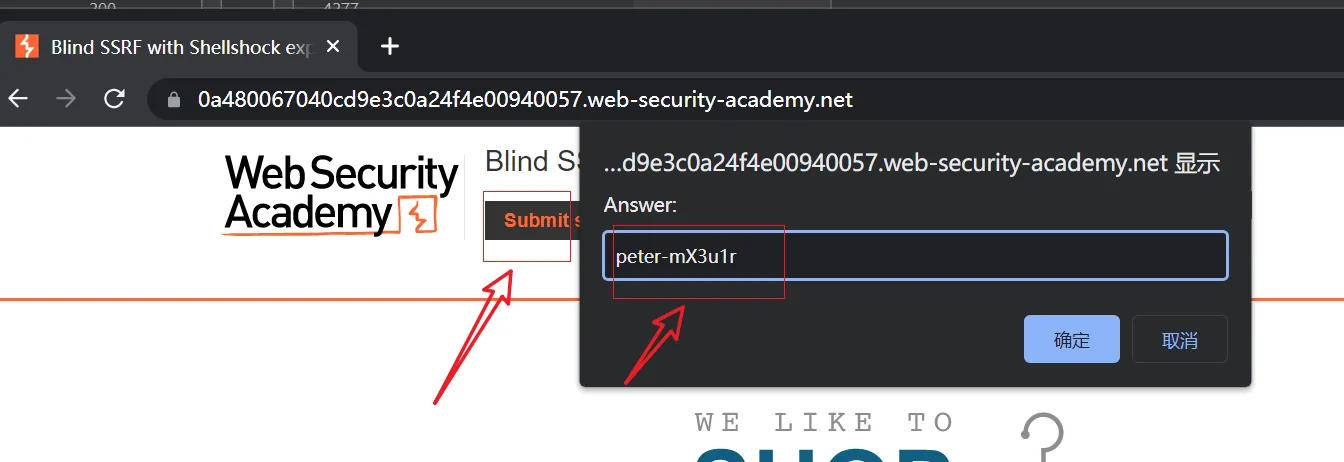
This site uses analytics software which fetches the URL specified in the Referer header when a product page is loaded. To solve the lab, use this
portswigger ssrf lab 服务器端请求伪造靶场- 🔰雨苁ℒ🔰
Portswigger Web Security Academy Lab: Blind SSRF with Shellshock
portswigger ssrf lab 服务器端请求伪造靶场- 🔰雨苁ℒ🔰

A GUIDE TO SERVER SIDE REQUEST FORGERY(SSRF) » Securityboat

SSRF盲打& Collaborator everywhere-CSDN博客
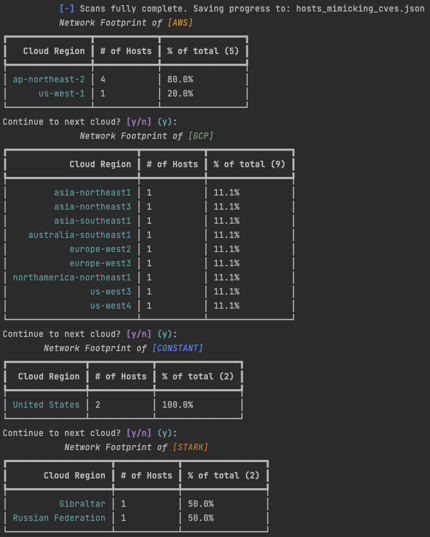
An Attacker's Guide to Evading Honeypots - Part 3
Portswigger Web Security Academy Lab: Blind SSRF with
Rana Khalil 🇵🇸 on X: 🧵 The Web Security Academy course has
Cracking the lens: targeting HTTP's hidden attack-surface
PortSwigger之SSRF+XXE漏洞笔记- FreeBuf网络安全行业门户

PortSwigger SSRF Labs. Hey all! This write-up is about my…
Server Side Request Forgery · master · pentest-tools

HackMD - Collaborative Markdown Knowledge Base
de
por adulto (o preço varia de acordo com o tamanho do grupo)