Issue 117: Vulnerabilities in and Ring Neighbors app, OAuth Mix-Up attacks, Tamper Dev - API Security News
Por um escritor misterioso
Descrição
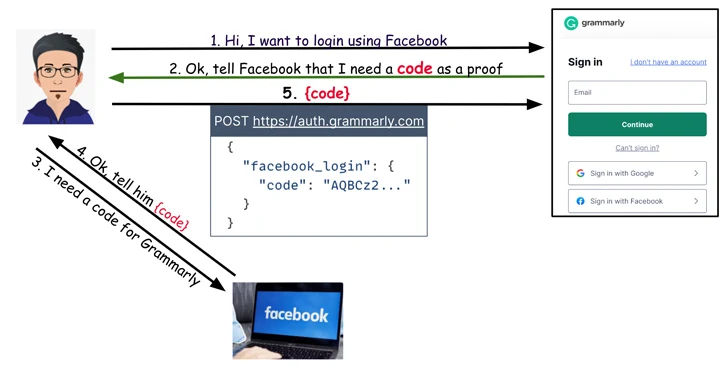
Critical OAuth Flaws Uncovered in Grammarly, Vidio, and Bukalapak Platforms

Sensors, Free Full-Text
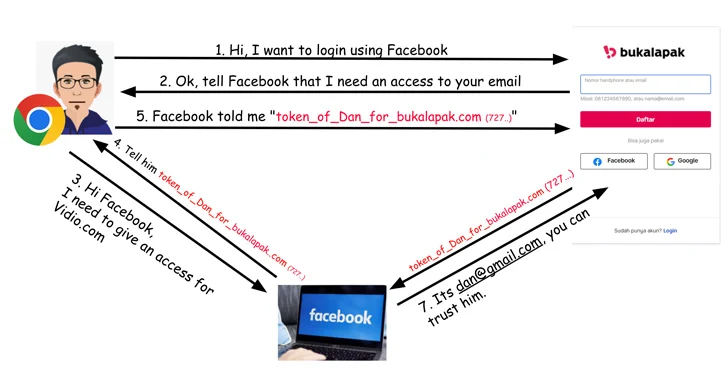
Critical OAuth Flaws Uncovered in Grammarly, Vidio, and Bukalapak Platforms

Authentication and authorization vulnerabilities and how to avoid them

Issue 117: Vulnerabilities in and Ring Neighbors app, OAuth Mix-Up attacks, Tamper Dev - API Security News

Web Parameter Tampering Attack on Web Servers - GeeksforGeeks

Supercharged

PDF) ISA 2012 Proceedings

Cloud Security Security PDF, PDF, Cloud Computing

PDF) CSCI 2021 BOOK of ABSTRACTS

Digital Humanities 2016
GitHub - koenbuyens/Vulnerable-OAuth-2.0-Applications: vulnerable OAuth 2.0 applications: understand the security implications of your OAuth 2.0 decisions.
de
por adulto (o preço varia de acordo com o tamanho do grupo)