Using an Incident-Focused Model for Information Security Programs
Por um escritor misterioso
Descrição
[nodOrganizations attempt to prevent information security incidents by embedding tools in policies and practices across business functions. Because it is not possible to completely prevent security events, organizations must also include proven response practices as part of their security program. e:summary]
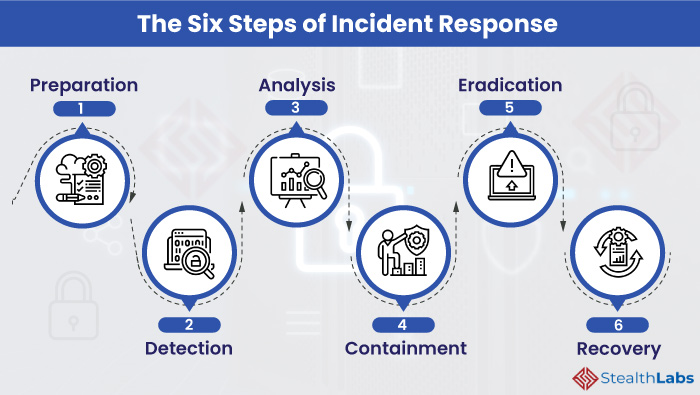
6 Steps to an Effective Cyber Incident Response Plan (+ Tips)
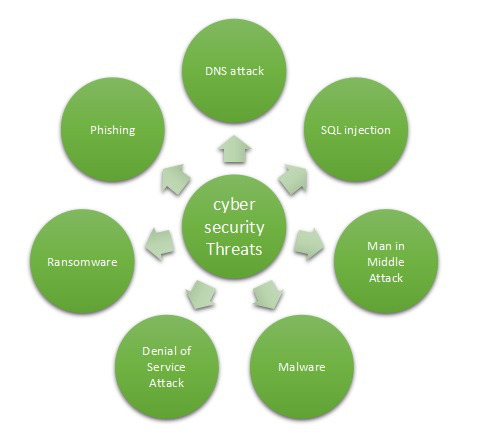
Cyber Security Policy - GeeksforGeeks

Security Operations, SecOps
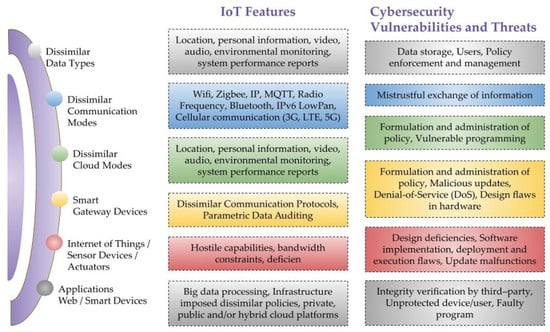
Sensors, Free Full-Text
Data incident response process, Documentation

What is the future of cybersecurity?

Table 1 from Isfam: the Information Security Focus Area Maturity
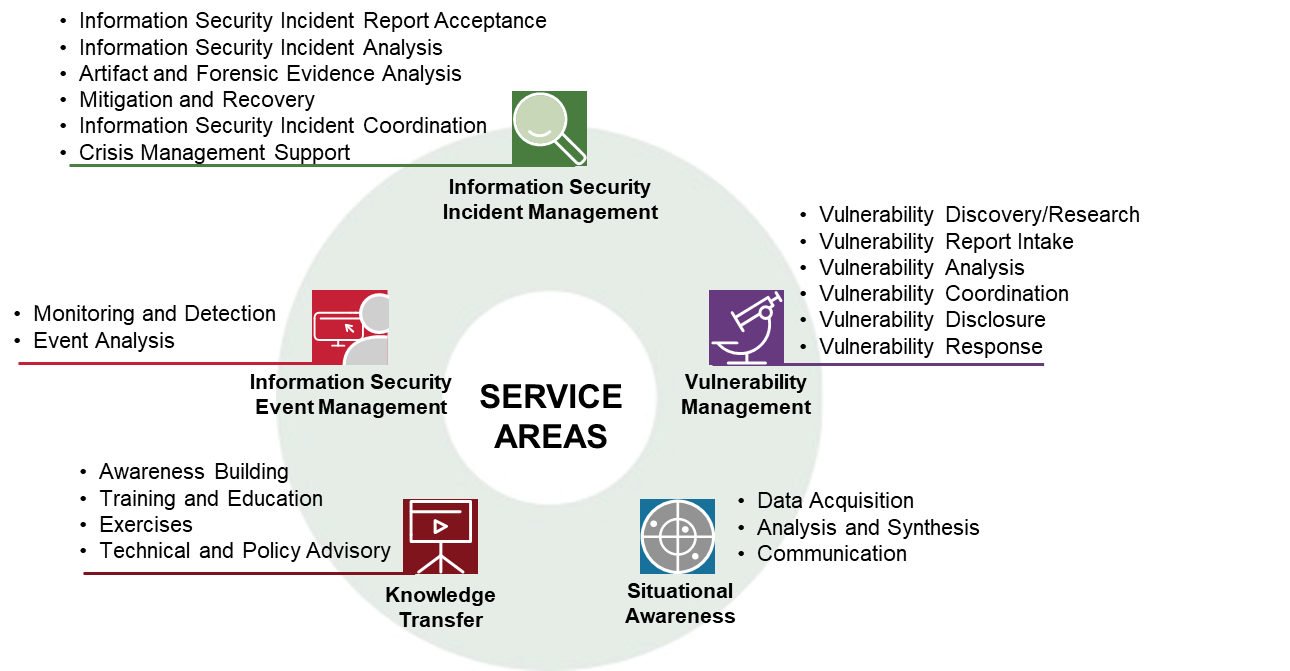
CSIRT Services Framework Version 2.1

What Is Information Security (InfoSec)? - Cisco

The Chief Information Security Officer (CISO) Role Explained – BMC

The Top 25 Cybersecurity Companies of 2021

NIST Incident Response: Your Go-To Guide to Handling Cybersecurity

Information Security Plan: Examples & Incident Response
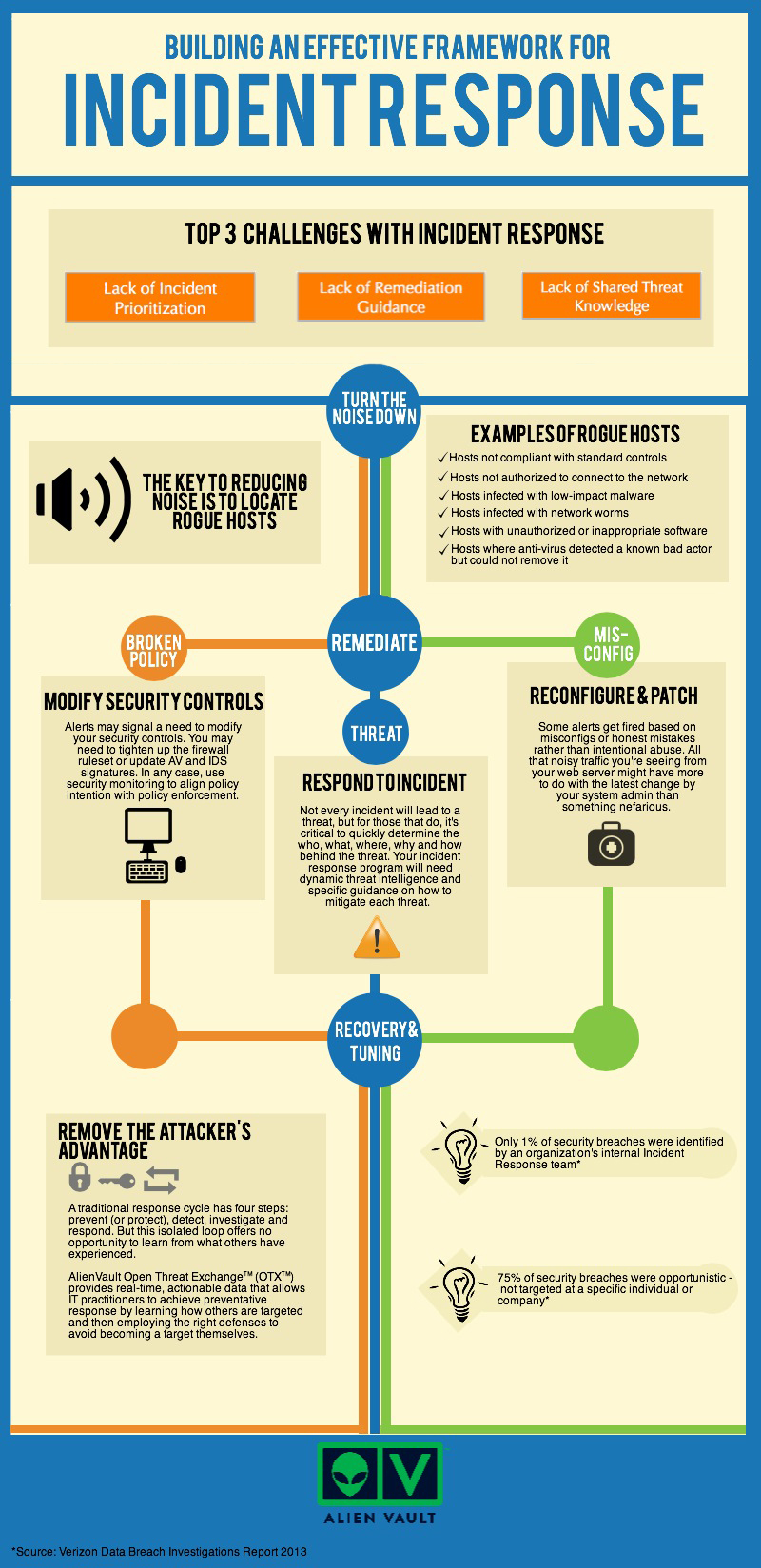
Building an Effective Incident Response Framework Infographic
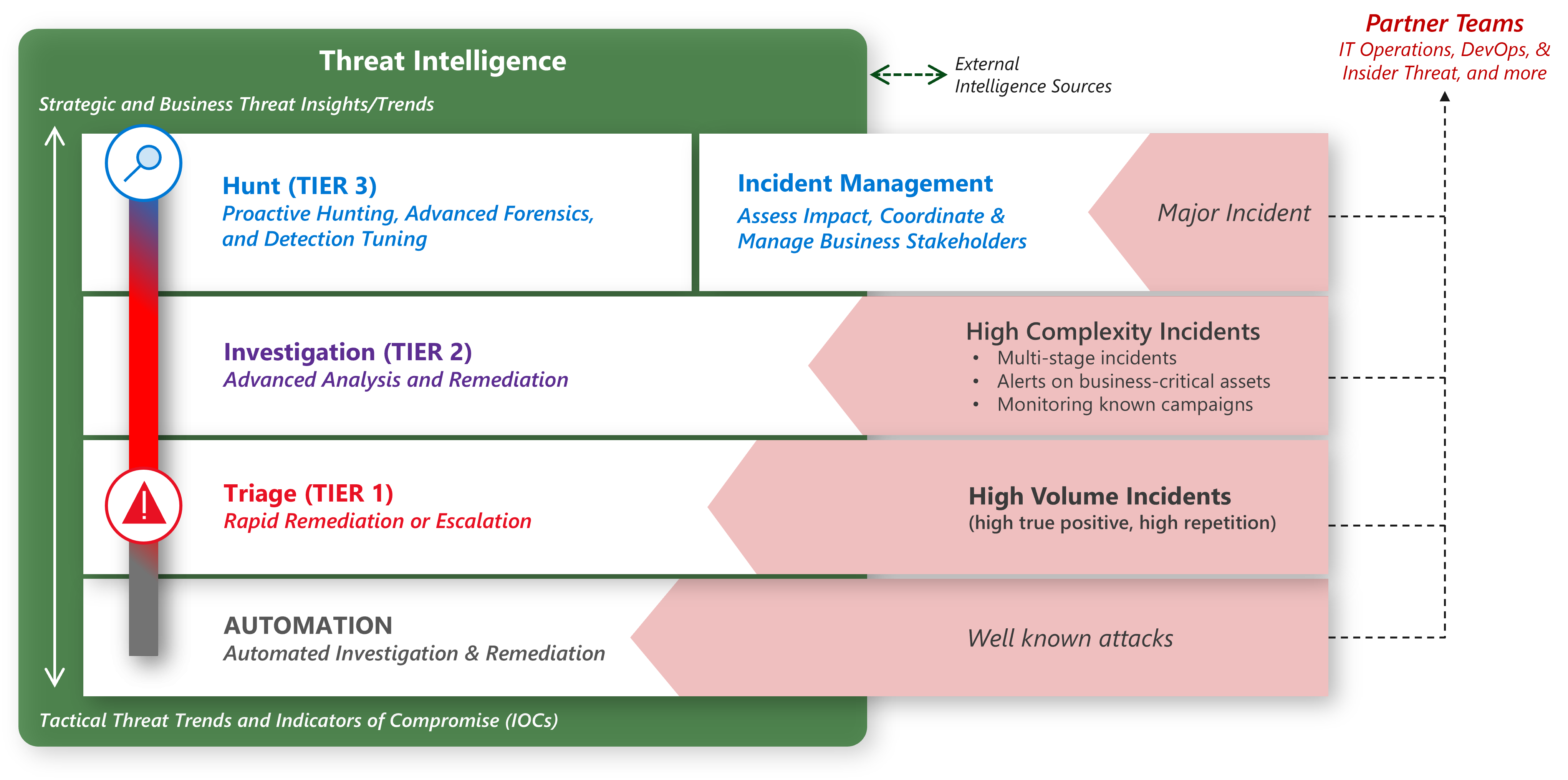
Security operations - Cloud Adoption Framework
de
por adulto (o preço varia de acordo com o tamanho do grupo)






_roblox-mod-apk-2-600-713-gameplay-2023-vip-unlimited-money-amp-robux-100-roblox-mod-menu-2-600-preview-hqdefault.jpg)