Abusing Exceptions for Code Execution, Part 1
Por um escritor misterioso
Descrição
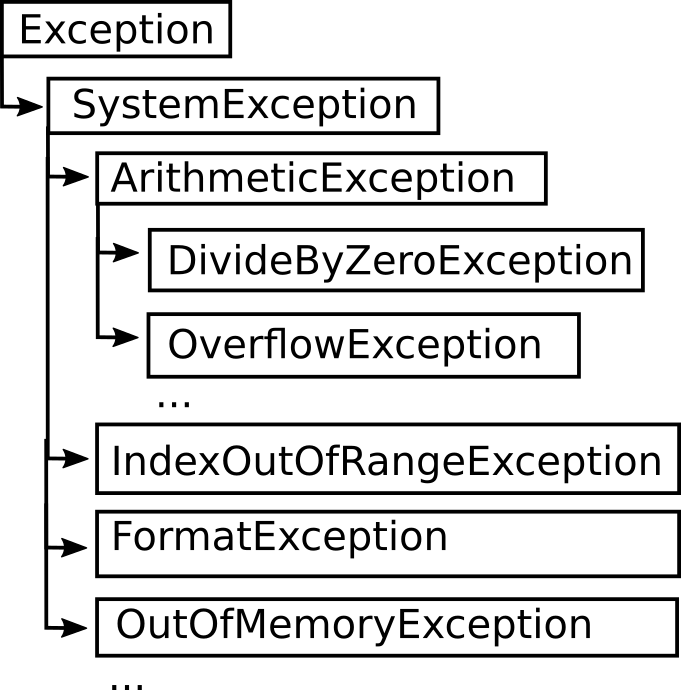
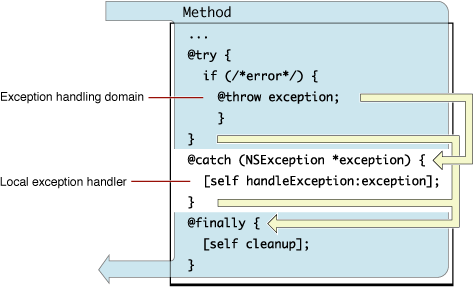
A common offensive technique used by operators and malware developers alike has been to execute malicious code at runtime to avoid static detection. Often, methods of achieving runtime execution have focused on placing arbitrary code into executable memory that can then be executed. In this article, we will explore a
A common offensive technique used by operators and malware developers alike has been to execute malicious code at runtime to avoid static detection. Often, methods of achieving runtime execution have focused on placing arbitrary code into executable memory that can then be executed. In this article, we will explore a new approach to executing runtime code that does not rely on finding executable regions of memory, but instead relies on abusing existing trusted memory to execute arbitrary code.
A common offensive technique used by operators and malware developers alike has been to execute malicious code at runtime to avoid static detection. Often, methods of achieving runtime execution have focused on placing arbitrary code into executable memory that can then be executed. In this article, we will explore a new approach to executing runtime code that does not rely on finding executable regions of memory, but instead relies on abusing existing trusted memory to execute arbitrary code.

Cybersecurity and digital trade: Getting it right

What are Code Smells in Angular?. In one of my previous post I talked…, by Robert Maier-Silldorff

Epigenetics - Wikipedia
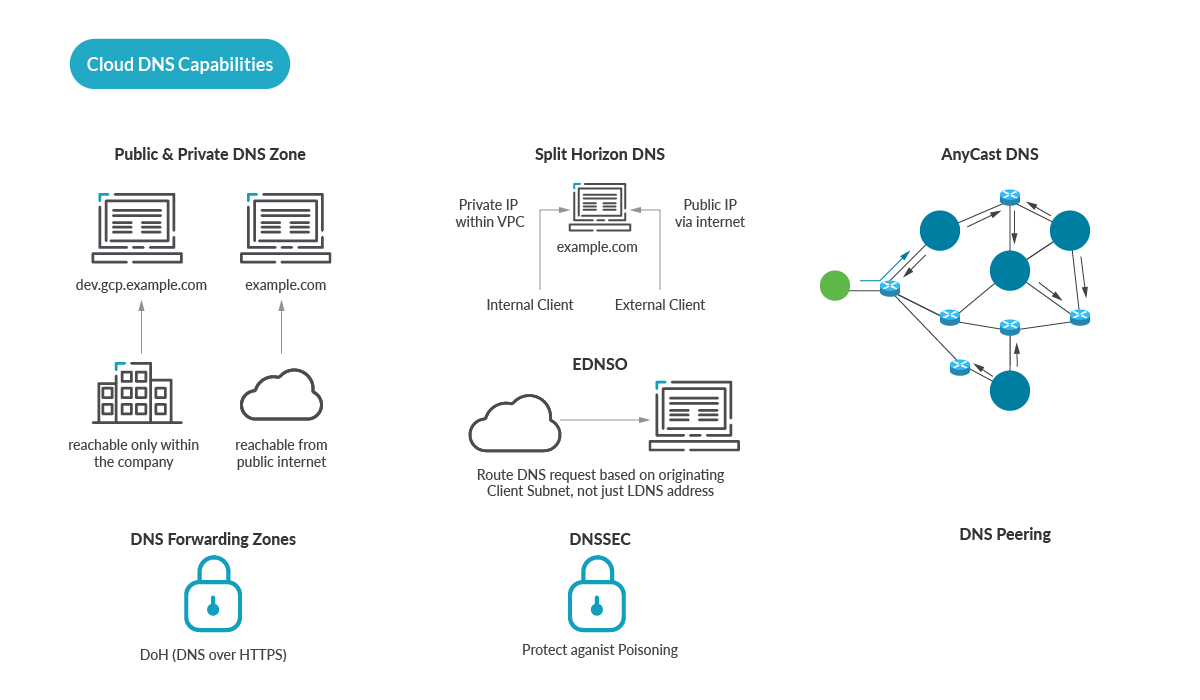
Cloud DNS Security - How to protect DNS in the Cloud – Sysdig
:max_bytes(150000):strip_icc()/ESOP_Final_4196964-2e25b96d22ce437497a38754c6c866ff.jpg)
Employee Stock Ownership Plan (ESOP): What It Is, How It Works, Advantages

Opioid Prescribing for Chronic Pain: Case Studies and Best Practices
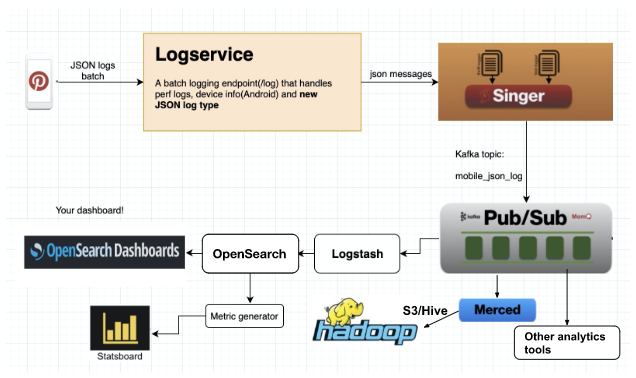
Build an end to end JSON logging system for clients apps, by Pinterest Engineering, Pinterest Engineering Blog

GitHub Actions Security Best Practices [cheat sheet included]

Sick leave abuse, poor performance and the disciplinary code - Labour Guide South Africa
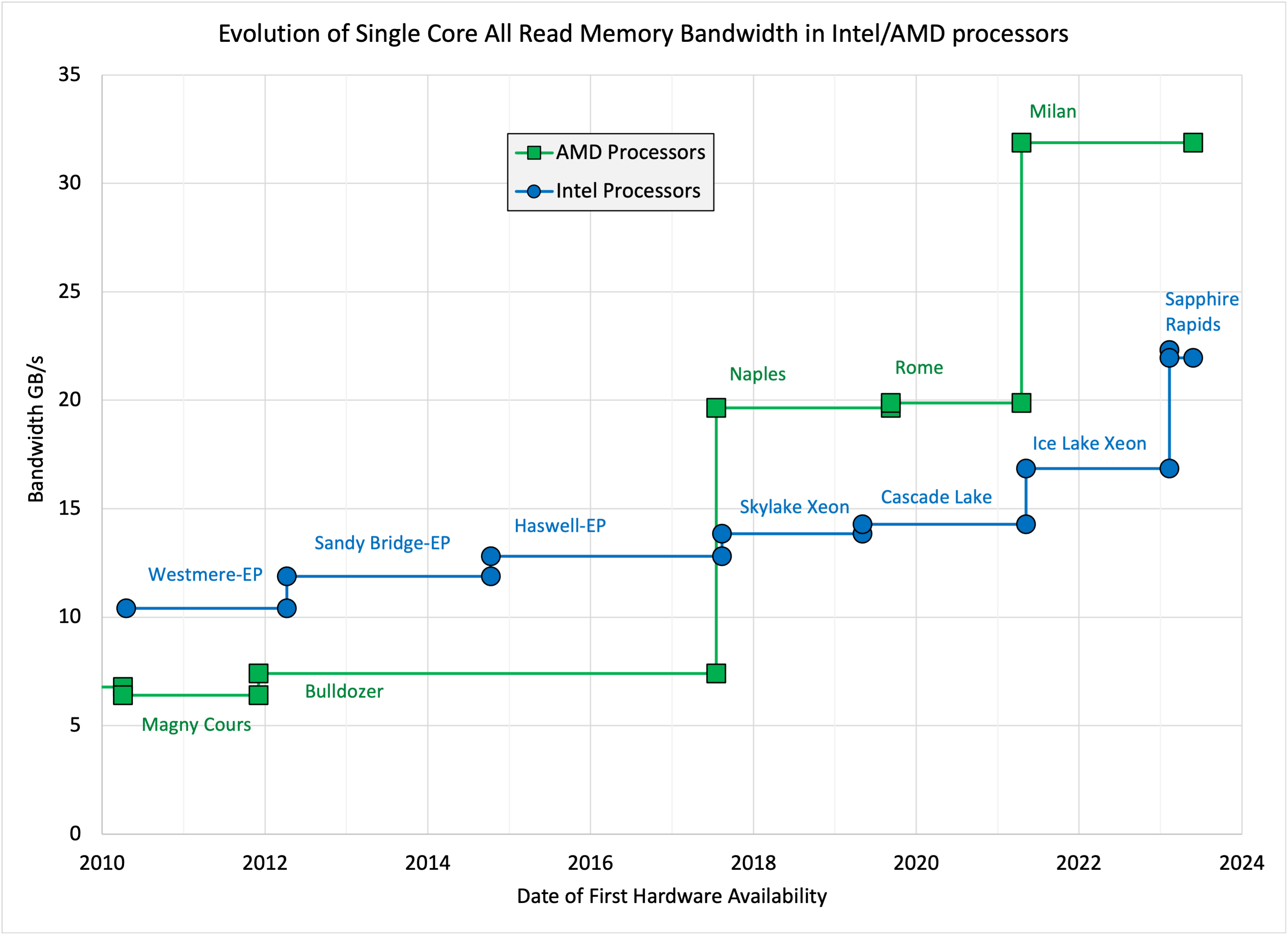
John McCalpin's blog » STREAM benchmark

What is Remote Code Execution (RCE) Vulnerability❓

mTLS: When certificate authentication is done wrong - The GitHub Blog
de
por adulto (o preço varia de acordo com o tamanho do grupo)